GuardDuty to Microsoft Teams
· 320 words · 2 minutes read
As part of my job I needed a way to monitor for breaches and potential threats on the AWS accounts used by my team, recently at re:invent AWS announced a new service GuardDuty to monitor for threats like EC2 instances that are breached and mining bitcoin, unusual API calls, and various other potential breaches. While having an automated response to all these potential situations would be ideal I thought the first step should be to get notified if something happens, and while email would work I already get way too much of that, so seeing as we use Microsoft Teams that seemed like the best case for new alerts that I will hopefully never see.
If you’re not familiar with Teams, it’s Microsoft’s answer to Slack, and while it has a ways to go, it’s not too bad. It supports web hooks where you can send a json payload to make a good looking card like so:
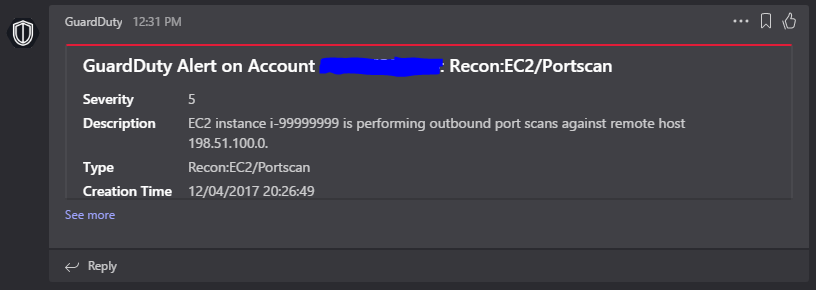
Sample notification from GuardDuty in Microsoft Teams
Ⓒ 2017 F5 Networks
In order to do this I created a lambda function that takes the event from GuardDuty and then formats them nicely and sends them to Teams, while that’s straightforward enough, actually sending an outbound connection takes a-lot of work from a lambda function, it requires a separate VPC with some subnets, NAT Gateway, Internet Gateway, and route tables to accompany it. I won’t bore you with the details but there is a CloudFormation template here on github, and below is the design output by CloudFormation.
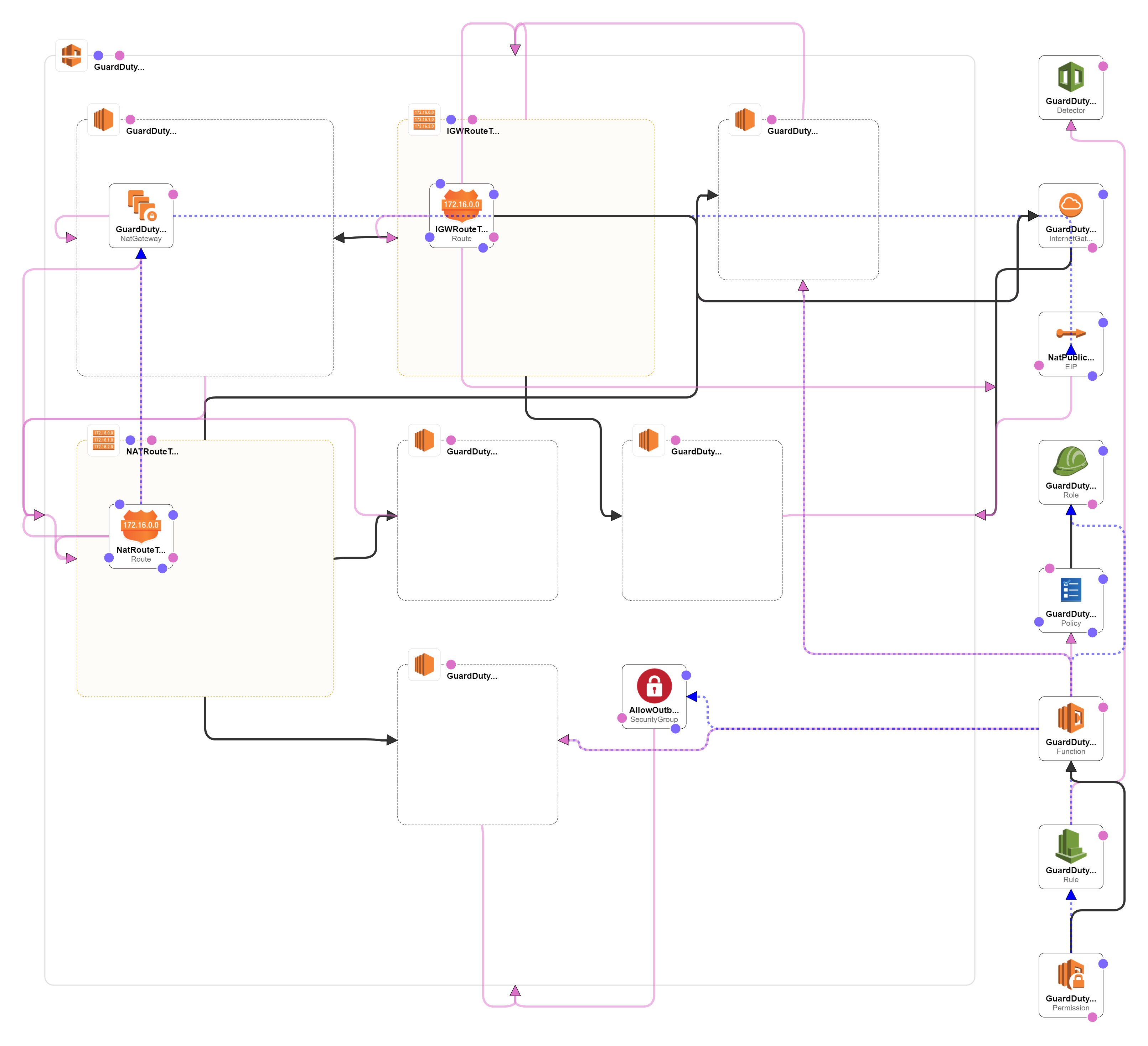
CloudFormation Diagram
Ⓒ 2017 F5 Networks
The good news is since deploying this I haven’t seen a single alert that was not a sample alert I expected, but on the day I get an unexpected alert I’ll be ready to react.
This post is not sponsored or endorsed by F5 Networks, I am just documenting some of my useful Open Source work which was done for them.